
Next-Gen App & Browser Testing Cloud
Trusted by 2 Mn+ QAs & Devs to accelerate their release cycles

On This Page
- What Is Boundary Value Analysis in Software Testing?
- How Boundary Value Analysis in Software Testing Works?
- Why Is BVA Crucial in Software Testing?
- What Are the Test Scenarios and Test Cases for Boundary Value Analysis?
- What Are the Various Techniques for Boundary Value Testing?
- What Are the Benefits of BVA for Input Validation?
- What Are Real-World Examples of Input Validation Using BVA for Different Data Types?
- How Can {`${BrandName}`} Help Execute Boundary Value Analysis?
- Which Tools Can Be Used to Implement Boundary Value Analysis in Test Automation?
- Which Common Mistakes Should Be Avoided in BVA?
- Best Practices for Considering Boundary Conditions in Testing
- Conclusion
- Citations
- Home
- /
- Learning Hub
- /
- What Is Boundary Value Analysis: A Complete Guide
What Is Boundary Value Analysis: A Complete Guide
Learn boundary value analysis in software testing with techniques, examples, automation tools, best practices, and common mistakes for input validation.
Onwuemene Joshua
January 11, 2026
Boundary Value Analysis (BVA) focuses on validating system behavior at defined input limits, where defects are most likely to surface due to boundary conditions and comparison logic. Rather than testing complete input ranges, BVA evaluates minimum, maximum, and immediately adjacent values to maximize defect detection with a limited set of test cases.
By concentrating on these critical input boundaries, Boundary Value Analysis in software testing improves input validation reliability, optimizes test effort, and supports scalable and cost-effective quality assurance practices.
Overview
How Does Boundary Value Analysis Help in Software Testing?
Boundary Value Analysis (BVA) is a black-box technique that tests inputs at the edges of allowed ranges to catch defects near limits. It focuses on minimum and maximum values, checks inputs just inside and outside boundaries, identifies off-by-one errors and incorrect comparisons, and reduces the number of test cases while maximizing defect detection.
What Is the Significance of Boundary Value Analysis in Software Testing?
BVA ensures testing focuses on critical input limits, uncovering defects while optimizing effort and coverage.
- Maximises Defect Detection with Minimal Test Cases: Strategically testing boundary inputs efficiently captures potential failures without executing an excessive number of redundant tests.
- Addresses the Root Cause of Common Programming Errors: Targets off-by-one mistakes and logical miscalculations that frequently appear around maximum or minimum values.
- Provides Systematic Coverage of Critical Input Ranges: Guarantees that edge conditions are consistently validated, ensuring no vulnerable boundaries are accidentally skipped.
- Complements Other Testing Techniques: Works alongside equivalence partitioning or exploratory testing to strengthen overall software quality and reliability.
- Reduces Testing Time and Costs: Minimizes unnecessary execution cycles, saving resources while maintaining thorough validation across boundary-related scenarios.
- Improves User Experience by Preventing Edge Case Failures: Detects input-related errors that could disrupt functionality, security, or data integrity for end-users.
- Supports Regulatory Compliance and Quality Standards: Helps meet software standards requiring explicit testing of extreme and critical input conditions for certification.
What Are the Techniques of Boundary Value Analysis in Software Testing?
BVA focuses on testing inputs at the edges of acceptable ranges, where most defects are likely to occur. Different techniques help balance coverage, risk, and testing effort effectively.
- Two-Value BVA: Tests only the minimum and maximum valid inputs to quickly validate boundary handling for low-risk features.
- Three-Value BVA: Adds values just inside boundaries to detect defects near limits and verify calculation or comparison logic.
- Robust BVA: Includes invalid boundary values along with valid ones to check system error handling, security, and compliance with strict input rules.
- Worst-Case BVA: Examines all boundary combinations across multiple input variables to ensure thorough coverage in complex or safety-critical systems.
What Is Boundary Value Analysis in Software Testing?
Boundary Value Analysis (BVA) is a black-box test design technique that focuses on testing values at the edges of input ranges, where most software defects occur. Rather than testing all possible values within a range, BVA strategically tests the minimum boundary, maximum boundary, and values immediately adjacent to these limits (one below and one above each boundary).
The idea is straightforward: errors often occur at boundaries because conditions in code frequently compare values against limits. Issues such as off-by-one mistakes or incorrect use of comparison operators (< vs >=) show up when inputs approach these limits.
For example, if a form accepts ages from 18 to 65, boundary tests would include 17, 18, 65, and 66, as these inputs are more likely to reveal validation errors than a middle value like 42.
How Boundary Value Analysis in Software Testing Works?
BVA checks input values at the edges of a defined range because defects often occur at these points. For any input range with a minimum value min and a maximum value max, BVA typically tests:
- min − 1: just below the lower boundary
- min: at the lower boundary
- min + 1: just above the lower boundary
- max − 1: just below the upper boundary
- max: at the upper boundary
- max + 1: just above the upper boundary
For example, company “ABC” is doing an end-of-the-year discount sale, but they only want to give a discount when a user orders 5 to 15 products. Meaning there is an invalid range and an accepted range. We can put it in a table.
Product Quantity
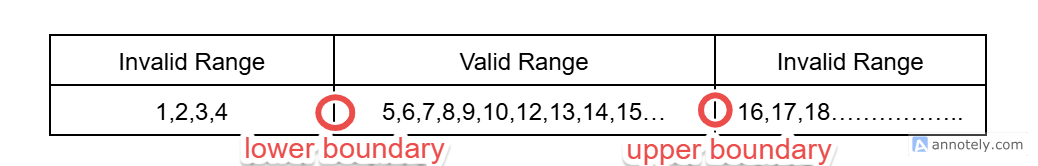
The test cases for this scenario will be:
| Test Cases | Boundary Description | Expected Results |
|---|---|---|
| Order placed with quantity: 4 | One unit below the lower boundary | Rejected |
| Order placed with quantity: 5 | At the lower boundary | Accepted |
| Order placed with quantity: 6 | One unit above the lower boundary | Accepted |
| Order placed with quantity: 14 | One unit below the upper boundary | Accepted |
| Order placed with quantity: 15 | At the upper boundary | Accepted |
| Order placed with quantity: 16 | One unit above the upper boundary | Rejected |
Note: Run automation tests across 3,000+ browser and OS combinations. Try TestMu AI Now!
Why Is BVA Crucial in Software Testing?
BVA is crucial in software testing because it helps you find defects that occur at input limits while keeping the number of test cases low.
It provides systematic coverage of critical boundaries, improves software quality, and strengthens the overall software testing lifecycle.
BVA also complements other test design techniques, helping you detect common edge-case errors that often go unnoticed in functional testing.
Some key reasons include:
- Maximises Defect Detection with Minimal Test Cases: Testing every possible input value is expensive and time-consuming. For a simple field accepting integers from 1 to 1000, BVA reduces this to just 6 test cases while catching the majority of boundary-related defects.
- Addresses the Root Cause of Common Programming Errors: Targets common programming errors like off-by-one errors and incorrect comparison operators that manifest at boundaries.
- Provides Systematic Coverage of Critical Input Ranges: Without BVA, testers might randomly select values to test or focus solely on valid inputs. This approach leaves gaps in test coverage, particularly at the edges where defects concentrate.
- Complements Other Testing Techniques: Works with equivalence partitioning and other testing techniques to provide comprehensive, multi-layered test coverage.
- Reduces Testing Time and Costs: Reduces test cases significantly without compromising quality, saving time on execution, maintenance, analysis, and overall costs.
- Improves User Experience by Preventing Edge Case Failures: Prevents user frustration, data loss, and security vulnerabilities caused by unexpected inputs at maximum or minimum limits.
- Supports Regulatory Compliance and Quality Standards: Meets regulatory requirements in standards such as ISO 9126 and IEC 62304, which mandate comprehensive boundary testing.
What Are the Test Scenarios and Test Cases for Boundary Value Analysis?
Knowing what BVA means is one thing, but understanding how to create effective test scenarios and test cases is the backbone for successful BVA implementation. It is also important to understand the distinction between a test scenario vs test case, as both play complementary roles in boundary testing.
A test scenario outlines what to test and covers a particular functionality or feature, while a test case provides the detailed steps, input values, and expected outcomes to execute that scenario.
The process involves:
- Identifying Input Boundaries: The first step in applying BVA is identifying all input boundaries in your application. Boundaries exist wherever there are defined ranges, limits, or constraints.
- Numeric ranges: Input fields like age (18–65) and quantity (1–100) should be tested at minimum and maximum boundaries.
- Text length constraints: Usernames (6–20 characters) and passwords (8–16 characters) require boundary testing to ensure proper validation and acceptance.
- Date ranges: Booking date inputs, from today to 90 days ahead, must be tested at both boundary limits.
- Array or collection sizes: Shopping cart items, ranging from 1 to 50, need boundary checks for minimum and maximum limits.
- Decimal precision: Price inputs, allowing up to two decimal places, should be validated at the lowest and highest allowed values.
- Regulatory requirements: Testing must comply with standards like ISO 9126 and IEC 62304 to cover all boundary-related scenarios.
- Structuring BVA Test Cases: A well-structured BVA test case includes the following key components:
- Test Case ID: A unique identifier used to track and reference the test case.
- Test Objective: Describes the specific boundary condition or scenario being tested.
- Input Boundary: Defines the input range or limit that the test focuses on.
- Test Data: Specifies the exact values at or near the boundaries to be tested.
- Expected Result: Indicates what the system should do when the test is executed.
- Actual Result: Records the system’s actual behavior during the test execution.
- Status: Marks the outcome of the test, usually Pass or Fail.
- Positive and Negative Test Scenarios: BVA naturally creates both positive and negative test scenarios:
- Positive Test Scenarios: Test values within valid boundaries, including the minimum boundary, just above the minimum, just below the maximum, and the maximum boundary, to confirm valid inputs are accepted.
- Negative Test Scenarios: Test values outside valid boundaries, such as just below the minimum, just above the maximum, and extremely invalid inputs to ensure proper rejection and robust error handling.
- Documentation Best Practices: Effective test case documentation ensures that anyone on the team can understand and execute your BVA tests:
- Clear Test Case Names: Use descriptive and meaningful names so each test case can be easily identified and understood.
- Valid Range in Description: Clearly mention the input range being tested, referencing values defined in the Software Requirement Specification(SRS) to ensure boundary conditions are accurate and aligned with business rules.
- Expected Error Messages: Document expected error messages for negative boundary scenarios to verify correct validation and user feedback.
- Preconditions or Test Data Setup: Note any required setup, assumptions, or dependencies based on system behavior defined in the requirements or SRS documentation.
- Screenshots or UI References: Include UI screenshots or references where applicable to support execution and faster debugging.
- Link Related Test Cases: Link boundary test cases back to related requirements in the SRS, improving traceability, audit readiness, and overall test coverage.
Common boundary scenarios include:
Password Length Validation (Range: 8-16 characters)
| Test Case ID | Input Value | Character Count | Expected Result |
|---|---|---|---|
| TC_PWD_001 | "Pass123" | 7 | Reject - Too short |
| TC_PWD_002 | "Pass1234" | 8 | Accept |
| TC_PWD_003 | "Pass12345" | 9 | Accept |
| TC_PWD_004 | "Pass123456789ab" | 15 | Accept |
| TC_PWD_005 | "Pass123456789abc" | 16 | Accept |
| TC_PWD_006 | "Pass123456789abcd" | 17 | Reject - Too long |
Positive scenarios confirm that valid inputs are accepted, while negative scenarios ensure invalid inputs are rejected, preventing false positives and false negatives that could degrade product quality and affect user experience.
What Are the Various Techniques for Boundary Value Testing?
Since failures frequently occur at boundary limits rather than within normal input values, this approach helps you detect errors related to validation logic, comparisons, and numerical calculations.
Below are the most commonly used BVA techniques, explained with real-world application examples to help you understand how they are applied in practical scenarios.
Two-Value Boundary Value Analysis
Two-Value BVA is the simplest form of BVA in software testing. In this technique, you test only the exact minimum and maximum values of an input range. It is typically used when you want to confirm that the system accepts values at its defined limits.
Real-World Example: An online exam system allows students to select between 1 and 100 questions for a practice test.
- 1: Minimum allowed number of questions
- 100: Maximum allowed number of questions
This verifies that the system accepts both boundary values without errors.
Two-Value BVA is Appropriate When:
- Basic Boundary Validation: Use two-value BVA when you need to quickly verify that the system correctly accepts input at the minimum and maximum defined limits.
- Low-Risk Functionality: Apply this technique for low-risk features where boundary failures are unlikely or have minimal impact.
- Early Test Phases: Use it during early testing stages to perform an initial check of boundary handling before applying more detailed techniques.
- Limited Time Constraints: Choose this approach when time or resources are limited and broad boundary coverage is sufficient.
Three-Value Boundary Value Analysis
Three-Value BVA extends two-value BVA by including a value close to the boundary. This technique helps identify defects that occur just inside the valid input range, which are common in systems with calculation or comparison logic.
Real-World Example: A banking application allows customers to transfer an amount between $1 and $50,000.
You test:
- $1: Minimum transfer amount
- $2: Just above the minimum
- $50,000: Maximum transfer amount
This helps ensure that small, valid transactions are processed correctly.
Three-Value BVA is Appropriate When:
- Near-Boundary Defect Detection: Apply three-value BVA when defects are likely to occur just inside the valid input range rather than exactly at the boundaries.
- Precision-Sensitive Logic: Use this technique for calculations or comparisons where small input changes can affect system behavior.
- Moderate Risk Areas: Choose a three-value BVA for features that require more coverage than a two-value BVA but do not justify robust or worst-case testing.
- Incremental Test Coverage: Use it when gradually increasing test depth while maintaining a manageable test case volume.
Robust Boundary Value Analysis
Robust BVA includes invalid boundary values in addition to valid ones. This technique is useful for verifying how the system handles incorrect or out-of-range inputs and whether proper error messages are displayed.
Real-World Example: A user registration form requires the age to be between 18 and 60 years.
You test:
- 17: Just below the minimum (invalid)
- 18: Minimum valid age
- 19: Just above the minimum
- 59: Just below the maximum
- 60: Maximum valid age
- 61: Just above the maximum (invalid)
Robust BVA is Appropriate When:
- High-Risk System Coverage: Apply Robust Boundary Value Analysis to mission-critical systems where failures are unacceptable, ensuring boundary-related defects do not cause system breakdowns.
- Security and Input Validation: Use this technique for applications exposed to potentially malicious or unexpected input to confirm that invalid boundary values are handled safely.
- Exception Handling Verification: Validate systems that require strong input checks and exceptional error handling to ensure errors are detected and managed correctly.
- Regulatory Compliance Assurance: Test financial, healthcare, and other compliance-driven applications to verify that boundary violations are properly restricted and logged.
Worst-Case Boundary Value Analysis
Worst-Case BVA is used when testing functions that involve multiple input variables. In this technique, you systematically test all possible combinations of boundary values across all inputs. If a system has n variables, each with five boundary-related values (minimum minus one, minimum, nominal, maximum, and maximum plus one), worst-case BVA produces 5ⁿ test cases.
Real-World Example: Consider a loan processing system with two input variables:
- Loan amount
- Loan term
Each variable has five boundary-related values. Worst-case BVA generates 25 test cases (5²) by testing every possible combination of these values. This approach ensures thorough coverage but becomes impractical as the number of variables increases beyond three or four.
Worst-Case BVA is Appropriate When:
- Complex Variable Interaction: Use Worst-Case Boundary Value Analysis when input variables interact in complex or dependent ways, ensuring boundary combinations do not trigger unexpected behavior.
- Historical Defect Coverage: Apply this technique when defects have previously occurred at the intersection of boundary conditions to prevent regression and recurrence.
- Safety-Critical Assurance: Choose worst-case BVA for safety-critical systems that require exhaustive testing to minimize the risk of boundary-related failures.
- Resource Availability Consideration: Implement this approach only when sufficient time and resources are available to support extensive test case execution.
Boundary value testing techniques help you detect defects that occur at the edges of input ranges, where systems are most likely to fail. By selecting the appropriate BVA technique, two-value, three-value, robust, or worst-case, you can balance test coverage, risk, and effort while improving software testing outcomes and overall system quality.
What Are the Benefits of BVA for Input Validation?
Input validation is the first line of defense against bad data, security vulnerabilities, and system instability. Applying BVA in software testing provides measurable benefits for ensuring that input validation works correctly.
- Comprehensive Edge Case Coverage: Ensures input validation handles minimum and maximum acceptable values, invalid inputs, and transitions between valid and invalid states, preventing failures at the extremes.
- Early Detection of Validation Errors: Targets common mistakes such as off-by-one errors, incorrect comparison operators, and miscalculated boundaries, allowing defects to be caught before they reach production.
- Data Integrity Assurance: By validating boundary cases, BVA prevents invalid data from entering the system, reducing the risk of corrupted databases, incorrect calculations, and system instability.
- Enhanced Security: Boundary testing helps identify vulnerabilities like buffer overflows and other exploits that rely on exceeding input limits, strengthening overall system security.
- Consistent User Feedback: Ensures that valid boundary values are accepted, invalid inputs trigger clear error messages, and users understand acceptable input ranges, improving usability and reducing confusion.
What Are Real-World Examples of Input Validation Using BVA for Different Data Types?
Understanding how to apply Boundary Value Analysis (BVA) to different data types strengthens practical software testing skills.
Here are examples across common input types.
- Numeric Data Types (Integer Values): In an e-commerce shopping cart, customers can order between 1 and 99 units of a product. Boundary Value Analysis ensures proper input validation during testing 0 (reject), 1 (minimum valid), 2 (just above minimum), 98 (just below maximum), 99 (maximum valid), and 100 (reject), preventing errors when users enter extreme quantities.
- Numeric Data Types (Decimal/Float Values): A payment system accepts transaction amounts from $0.01 to $10,000.00 with two decimal places. Applying BVA in Quality Assurance(QA) validates $0.00 (reject), $0.01 (minimum valid), $0.02 (just above minimum), $9,999.99 (just below maximum), $10,000.00 (maximum valid), and $10,000.01 (reject), ensuring accurate handling of financial transactions and contributing to quality software.
- String Data Types (Length Validation): A social media platform requires usernames between 3 and 15 characters. BVA checks 2-character usernames (reject), 3 characters (minimum valid), 4 characters (just above minimum), 14 characters (just below maximum), 15 characters (maximum valid), and 16 characters (reject). Testing additional boundaries such as empty strings, single characters, special characters, and leading/trailing spaces aligns with the principles of software testing to ensure consistent username validation.
- Date and Time Data Types: A venue booking system allows reservations from today up to 365 days in the future. BVA tests include yesterday (reject), today (minimum valid), tomorrow (just above minimum), 364 days ahead (just below maximum), 365 days ahead (maximum valid), and 366 days ahead (reject). Edge cases such as February 29 on a non-leap year, December 31 at 11:59 PM, and January 1 at 12:00 AM help enforce robust testing for date and time inputs.
- Time-Specific Boundaries: A restaurant accepts reservations between 5:00 PM and 10:00 PM. BVA verifies 16:59 (reject), 17:00 (opening time), 17:01 (just above minimum), 21:59 (just below maximum), 22:00 (last reservation time), and 22:01 (reject), supporting quality assurance by ensuring correct handling of operational hours.
- Email Address Validation: An email field follows RFC 5321 standards, with a local part up to 64 characters and a total length up to 254 characters. BVA tests 63 characters before @ (accept), 64 characters (maximum valid), 65 characters (reject), 253-character total (accept), 254-character total (maximum valid), and 255-character total (reject), validating both local and full email length boundaries and contributing to the delivery of software quality.
Building on these examples, Boundary Value Analysis becomes even more important in cloud-based platforms, where dynamic scaling, multi-tenancy, and variable resource limits can expose edge-case defects that might not appear in traditional environments.
Cloud applications introduce complexities like multi-user access, dynamic scaling, and distributed services. Applying BVA ensures input limits, API quotas, and data boundaries are validated, preventing performance issues, crashes, and security risks. Using automation testing tools on cloud platforms allows efficient execution of BVA test cases across devices and browsers.
One such platform is TestMu AI, which supports scalable cloud-based test automation for boundary validation.
How Can TestMu AI Help Execute Boundary Value Analysis?
TestMu AI is a cloud testing platform that enables teams to perform automation testing at scale across 3000+ browsers and 10,000+ real devices and OS combinations, making it easier to validate boundary conditions as part of a comprehensive cloud testing strategy.
Key features of TestMu AI for BVA in cloud testing:
- Scalable Cloud Infrastructure: Its cloud-based platform lets teams run automated tests in parallel, reducing execution time and enabling extensive boundary value test coverage without maintaining an on-premise device lab.
- Parallel Test Execution: You can execute multiple automation scripts simultaneously across different configurations, which is essential for validating many boundary test cases efficiently.
- Fast and Reliable Execution: It's nfrastructure is designed for high performance, with features like HyperExecute for faster automated test runs, helping verify boundary behavior quickly.
- Cross-Framework Support: It supports a wide range of automation frameworks (Selenium, Cypress, Appium, Playwright, etc.), so you can implement BVA regardless of your toolchain.
- Data-Driven Testing Support: Integration with data sources (e.g., CSV, Excel) and automation frameworks allows you to feed multiple boundary values into tests, which is critical for systematic BVA.
- Detailed Reporting and Debugging: Built-in analytics, logs, screenshots, and execution reports help you analyze boundary test results and debug failures efficiently.
- Secure, Enterprise-Ready Platform:Offers secure testing with enterprise-grade compliance, making it suitable for professional quality assurance and boundary validation workflows in the cloud.
Which Tools Can Be Used to Implement Boundary Value Analysis in Test Automation?
Modern software testing tools support BVA through features like parameterization, data-driven testing, and assertions. These tools allow testers to automate BVA test cases, validate boundary conditions consistently, reduce manual effort, and improve overall test efficiency in both web and application testing projects.
Selenium WebDriver
Selenium is the most popular open-source web automation tool, enabling testers to implement BVA across multiple browsers and platforms.
How it supports BVA:
- Parameterized Test Cases: Allows creation of boundary value tests using parameterization with frameworks like TestNG or JUnit, ensuring systematic coverage.
- Cross-Browser Verification: Validates boundary behavior across different browsers and environments to detect inconsistencies.
- Data-Driven Testing: Supports testing boundary values with Excel, CSV, or other data sources for efficient automation.
- Clear Assertions: Ensures that boundary responses are correctly validated, improving test reliability.
To learn more about how Selenium WebDriver helps you in performing test automation and cover all your edge cases, check out this Selenium WebDrivertutorial.
TestNG
TestNG is a Java testing framework that excels at creating parameterized boundary value tests with structured data management.
How it supports BVA:
- Boundary Parameterization: Uses @DataProvider to supply boundary values systematically, reducing manual test effort.
- Expected Result Validation: Enables specifying test data with expected outcomes for accurate verification.
- Organized Test Scenarios: Ensures boundary tests are clearly structured, improving maintainability.
- Assertion Integration: Works with multiple assertion libraries to verify boundary conditions consistently.
To learn more, check out this TestNG tutorial to see how the framework helps perform test automation and cover all boundary cases efficiently.
Apache JMeter
Apache JMeter, primarily known for load testing, also supports functional testing with boundary condition validation.
How it supports BVA:
- Parameterized Boundary Values: Uses CSV Data Set Config to feed boundary values into test scenarios.
- Boundary Assertions: Validates responses at boundaries to ensure correct behavior under edge conditions.
- Pre- and Post-Processors: Calculate and manipulate boundary values for precise testing.
- API Boundary Testing: Supports testing of API endpoints with boundary inputs to catch edge-case failures.
HP UFT (Unified Functional Testing)
HP UFT is a commercial tool supporting multiple technologies for functional testing, including boundary conditions.
How it supports BVA:
- Multi-Language Support: Enables scripting in various languages for flexible boundary testing.
- UI Boundary Verification: Uses visual object recognition to test boundary behavior in graphical interfaces.
- Data-Driven Testing Framework: Validates multiple boundary inputs efficiently through automated data sources.
- Built-in Boundary Validation: Includes native functions to check boundaries and expected outcomes.
- Test Management Integration: Connects with ALM to organize and track BVA test results systematically.
Rational Functional Tester (IBM)
IBM's Rational Functional Tester supports boundary testing across graphical and non-graphical user interfaces.
How it supports BVA:
- Multi-UI Technology Support: Tests boundaries across different interface technologies reliably.
- Data-Driven Boundary Testing: Uses parameterized data inputs for systematic boundary validation.
- Keyword-Driven Testing: Simplifies boundary test creation using reusable keywords.
- Robust Object Recognition: Ensures that boundary-sensitive elements are accurately identified during tests.
Cucumber/Gherkin (BDD Framework)
Cucumber allows writing boundary value test scenarios in plain English using Gherkin syntax, making tests understandable for technical and non-technical stakeholders.
How it supports BVA:
- Plain-Language Scenario Creation: Enables easy definition of boundary tests, improving collaboration.
- Parameterized Test Data: Supports feeding boundary values into scenarios systematically.
- Clear Expected Outcomes: Ensures that boundary tests specify results explicitly for accurate validation.
- Reusable Step Definitions: Allows repeated use of boundary test steps across scenarios for consistency.
To learn more, check out this Cucumber testing tutorial to see how the framework helps perform test automation and efficiently cover all boundary cases.
Which Common Mistakes Should Be Avoided in BVA?
When implementing BVA in software testing, a common mistake is assuming boundary tests alone provide full coverage. Overlooking these can lead to missed defects, which goes against the core principles of software testing. Always combine BVA with other testing strategies for reliable results.
Some common mistakes include:
- Ignoring Internal Boundaries: Testers focus only on external input limits, missing internal logic boundaries.
- Solution: Identify all internal limits during requirement analysis and include them in your BVA test cases. Following the principles of software testing, ensure both external and internal boundaries are validated.
- Example: In a hotel booking system, test not just the maximum booking days but also the room occupancy limits.
- Lacking Clear Boundary Definitions: Ambiguous requirements lead to ineffective test cases.
- Solution: Clarify boundary definitions with stakeholders before designing tests. Document precise min/max values to guide accurate BVA test creation.
- Example: Define the exact username length (e.g., 5–25 characters) to test minimum, maximum, and near-boundary values effectively.
- Ignoring Interaction Between Boundaries: Testing inputs individually can miss defects triggered by combinations.
- Solution: Use combinatorial or worst-case boundary analysis to test multiple inputs together. Ensure test coverage for interactions aligns with software testing principles.
- Example: In a loan system, test combinations of minimum loan amount with maximum term to uncover hidden defects.
- Not Updating BVA Tests with Requirement Changes: Boundaries change over time, but test cases remain outdated.
- Solution: Establish a process to review and update BVA test cases whenever requirements evolve. Keep a traceability matrix to track boundaries against current specifications.
- Example: If a password length requirement changes from 8–16 characters to 10–20 characters, update all BVA test cases to reflect the new minimum, maximum, and near-boundary values.
- Over-Relying on BVA Alone: Assuming boundary testing covers everything may neglect other defect types.
- Solution: Combine BVA with equivalence partitioning, exploratory testing, and scenario-based testing to ensure comprehensive coverage, in line with principles of software testing.
- Example: In an e-commerce checkout flow, BVA can validate quantity limits, but exploratory and scenario-based testing are needed to uncover defects related to payment failures, discount logic, session timeouts, or invalid user journeys.
Best Practices for Considering Boundary Conditions in Testing
Here are some of the best practices to consider when implementing boundary conditions.
- Conduct Thorough Boundary Discovery: Before creating test cases, systematically identify all boundaries in your application.
- Verify System Behaviour Under Boundary Conditions: Always verify that the system behaves exactly as expected when boundary conditions are met, not just that it accepts or rejects values.
- Use Realistic Test Data: Create boundary test cases using realistic data that mirrors actual user input patterns.
- Combine BVA with Equivalence Partitioning: Use both techniques together: BVA tests boundaries between equivalence partitions, while equivalence partitioning validates that all values within a range behave the same.
- Include Negative Testing at Boundaries: Don't just test that valid values are accepted: thoroughly test that invalid boundary values are rejected with appropriate error handling.
- Test Cross-Boundary Interactions: When multiple inputs interact with each other, test how boundaries in one input affect boundaries in another.
Conclusion
Boundary Value Analysis stands as one of the most effective and efficient testing techniques. The power of BVA lies in its fundamental principle: errors concentrate at boundaries. By strategically focusing testing efforts on these high-risk areas, QA teams achieve exceptional defect detection rates while dramatically reducing the number of test cases required. This efficiency doesn't compromise quality; it enhances it, allowing limited testing resources to have maximum impact.
Citations
- Boundary Value Analysis in Software Testing: https://kthmcollege.ac.in/AQAR/aqar_docs/aqar-2022-2023-3-1716613084546.Sci._BBDAREKAR_5.pdf.pdf
- Boundary Value Exploration for Software Analysis: https://ieeexplore.ieee.org/document/9155629
- Boundary Value Testing: https://bca.klesnc.edu.in/wp-content/uploads/2025/07/Software-Testing-Unit-1-Study-Material.pdf
Frequently asked questions
Did you find this page helpful?
TestMu AI forEnterprise
Get access to solutions built on Enterprise
grade security, privacy, & compliance
- Advanced access controls
- Advanced data retention rules
- Advanced Local Testing
- Premium Support options
- Early access to beta features
- Private Slack Channel
- Unlimited Manual Accessibility DevTools Tests



